
In the fast-paced, trillion-dollar programmatic advertising ecosystem, ad fraud remains a persistent and evolving threat, draining an estimated $80–100 billion annually from global ad budgets. Fraudulent activity takes many shapes—domain spoofing, botnets, click farms, and manipulated server-side ad insertions (SSAI)—and threatens advertiser confidence in digital channels.
The Trade Desk (TTD), a leading demand-side platform (DSP) that processes trillions of ad impressions monthly across display, video, audio, connected TV (CTV), mobile, and web, has long recognized this challenge. To fortify its marketplace, TTD integrated HUMAN Security (formerly White Ops), embedding advanced pre-bid and post-bid fraud defenses directly into its platform.
This collaboration represents a benchmark for fraud-resilient advertising in 2025, ensuring advertisers not only prevent wasteful spend but also preserve trust, optimize return on ad spend (ROAS), and strengthen the integrity of the open internet.
The Genesis: Why TTD Needed HUMAN’s Expertise
Programmatic advertising is an open marketplace, and that openness invites abuse. Fraudsters exploit:
- Spoofed domains: Misrepresenting low-quality inventory as premium.
- Hijacked devices: Botnets injecting fake traffic.
- SSAI manipulation: Generating counterfeit streaming ad views.
- Arbitrage schemes: Unauthorized reselling through broken supply chains.
The result? Inflated CPMs, skewed performance metrics, and wasted marketing dollars.
In 2017, TTD pioneered a shift from reactive fraud management to proactive prevention by becoming the first major DSP to implement HUMAN’s Human Verification technology across its platform. Instead of refund-chasing after fraud occurred, TTD embedded real-time blocking into its core workflows—aligning with its “objectively better inventory” philosophy.
By 2025, with fraudsters now leveraging AI-driven mimicry and multi-channel hopping, the TTD-HUMAN partnership has matured into a global defense network, disrupting operations at scale and setting new industry standards.
The Joint Defense Model: Closed-Loop Protection
HUMAN powers TTD’s fraud detection through a two-layer closed-loop system that blends real-time blocking with iterative learning.
1. Pre-Bid Decisioning – The Enforcement Wall
- HUMAN’s MediaGuard scans each bid request in under 100ms, scoring for invalid traffic (IVT).
- Flags both General IVT (GIVT) such as bots/crawlers, and Sophisticated IVT (SIVT) like malware-driven bots, spoofed devices, and SSAI fakery.
- Integrated via SDKs/APIs so TTD can filter high-risk impressions before bidding.
- Benefit: Advertisers avoid wasting spend, particularly in CTV and audio where risks are higher.
2. Post-Bid Confirmation – The Feedback Loop
- HUMAN’s FraudSensor validates impressions after delivery with telemetry data.
- Feeds insights back into pre-bid systems, tuning algorithms against real-world fraud patterns.
- Example: If anomalies cluster around a certain reseller, future requests from that path are flagged automatically.
- Benefit: Continuous learning reduces false positives and adapts to AI-evolving fraud tactics.
| Layer | Tools | Key Outcomes for TTD Buyers |
|---|---|---|
| Pre-Bid | MediaGuard (real-time scoring) | Blocks 99%+ of SIVT before bidding; zero-latency impact on auctions |
| Post-Bid | FraudSensor (telemetry + analytics) | Validates and refines; highlights vulnerable supply paths |
| Closed-Loop | Continuous feedback, MRC-accredited | Reduces false positives; future-proofs against AI-driven threats |
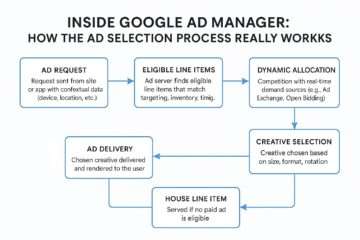
Workflow Integration: HUMAN Within TTD’s Ecosystem
The partnership is not an “add-on” but a core layer in TTD’s infrastructure:
- Supply Intake & Filtering
Bid requests from SSPs are analyzed for IP reputation, TLS/JA3 fingerprints, SDK hints, and SupplyChain Object (SCO) lineage. Unauthorized resellers or mismatches are blocked before TTD’s auction logic engages. - Optimization & Pacing
HUMAN’s post-bid analytics feed into TTD dashboards, allowing buyers to adjust frequency caps, shift spend to verified sellers, and avoid compromised supply paths. - Governance & Collective Defense
TTD is an active member of The Human Collective, a consortium sharing threat intelligence and coordinating takedowns. This means buyers benefit not just from TTD’s defenses, but also from an industry-wide safety net.
Channel-Specific Applications
Fraud looks different across formats. HUMAN-TTD integration adapts accordingly:
- CTV & Streaming: Blocks SSAI manipulation and spoofed devices (a growing fraud vector as CTV ad budgets surge).
- Audio & Podcasts: Protects against bid spoofing and SSAI exploits—a high-growth but vulnerable channel.
- Mobile & In-App: Flags device emulation and unnatural click patterns from farms or SDK abuse.
- Web & Display: Counters domain spoofing and iframe injection, using SCO validation to keep supply chains transparent.
Case Study: Operation “Apollo” (2025)
In April 2025, TTD and HUMAN’s Satori Threat Intelligence team exposed “Apollo”, the largest audio ad fraud scheme ever recorded:
- 400M fake bid requests per day at its peak.
- Exploited SSAI manipulation + residential proxies.
- Laundered traffic via unauthorized SCO paths.
- Represented ~10% of programmatic audio traffic globally.
Outcome: Within weeks, MediaGuard flagged anomalies while FraudSensor validated suspicious flows, reducing Apollo’s traffic by 99%. TTD buyers saw near-zero exposure, saving millions in potential wasted spend.
This case demonstrated how DSP-scale intelligence + specialist detection can dismantle even industrial-grade fraud operations.
HUMAN’s Fraud Detection Taxonomy
HUMAN evaluates risk across two major categories:
- GIVT (General IVT):
Data-center IPs, crawlers, automation headers, mismatched user agents. - SIVT (Sophisticated IVT):
- Device/app spoofing
- SSAI stream tampering
- CTV laundering
- Bot farms with behavioral mimicry
- SCO path discrepancies
Machine learning plus behavioral analysis ensures detection even when fraudsters attempt AI-driven camouflage.
Benefits for TTD Advertisers
- Cleaner Supply Chains: Spend redirected toward verified SCO-compliant inventory.
- Stable Campaign Outcomes: Lower IVT means more predictable reach, frequency, and ROAS.
- Granular Diagnostics: Campaign-level fraud reports allow custom allow/block lists.
- Regulatory Alignment: MRC accreditation supports audits and compliance.
- Competitive Edge: Fraud protection becomes a value-add for brands in a crowded DSP marketplace.
Operationalizing Fraud Defense in TTD
For buyers, best practices include:
- Enforce Supply Controls: Require sellers.json + SCO verification; block anomalies proactively.
- Tighten Pre-Bid Filters: Apply stricter HUMAN segments for CTV/audio.
- Iterate with Post-Bid Reports: Weekly reviews → export negatives → optimize bids.
- Sync Finance & Measurement: Align “clean impressions” with attribution/billing.
- Stay Engaged in Ecosystem: Leverage Human Collective alerts to anticipate cross-channel threats.
Why the Partnership is Defensible Over Time
Ad fraud is not static—schemes evolve alongside the ad tech stack. But TTD-HUMAN’s model creates a deterrence flywheel:
- Rapid detection → blocking → takedowns.
- Shared intelligence through The Human Collective.
- AI-enhanced models adapting to bot mimicry.
- Continuous improvement via closed-loop learning.
From 2017’s pioneering pre-bid integration to 2025’s Apollo takedown, the collaboration proves that fraud defense is not just a compliance checkbox—it’s a strategic moat for platforms and advertisers alike.
Final Thoughts
In a world where every wasted impression undermines trust, the TTD-HUMAN partnership demonstrates how real-time, ecosystem-level defense can keep programmatic advertising resilient.
It’s not simply about stopping fraud—it’s about ensuring advertisers get what they pay for: human attention.